There are errors (bugs) and security vulnerabilities in the code of almost all software. The more extensive the code, the more there are. Many of these security flaws are discovered over time by users or even by the manufacturer itself and plugged with a patch or the next update. Some, however, are first tracked down by criminal hackers who first keep this knowledge to themselves. They then either use the security hole themselves to penetrate other people’s systems, or they sell their find, often for horrendous sums.
What is a zero day flaw?Such newly discovered security vulnerabilities are called zero days, sometimes also spelled 0-day. This refers to the amount of time the manufacturer has to close the gap. “Zero days” means that the company has no time at all to develop a patch and publish it. This is because the hackers are already actively exploiting the vulnerability. To do so, they use a zero-day exploit, i.e. a method specially developed for this vulnerability, and use it to carry out a zero-day attack.
As soon as the software manufacturer learns about the vulnerability, it can develop a patch that specifically changes the responsible part of the code. Or it publishes an update, i.e. a revised and cleaned-up version of his program. As soon as a patch or an update exists, the exploit is no longer effective, the zero-day threat is officially over.
However, since many users do not apply patches immediately, but only after a few days or weeks delay, the danger posed by the vulnerability remains for a while.
Zero-day attacks are among the most dangerous of all. Because as long as the vulnerability is unknown to manufacturers and users, they do not take any preventive protective measures. For days, sometimes weeks or months, the attackers can scout out other people’s computer systems unnoticed, obtain higher rights, download confidential data, or install malware. Anti-virus tools are designed to detect such activities. Nevertheless, attackers succeed time and again in disguising themselves so well that they sometimes remain undetected.
Further reading: The best antivirus software for Windows PCs
Coveted secret information: Prizes of a million and more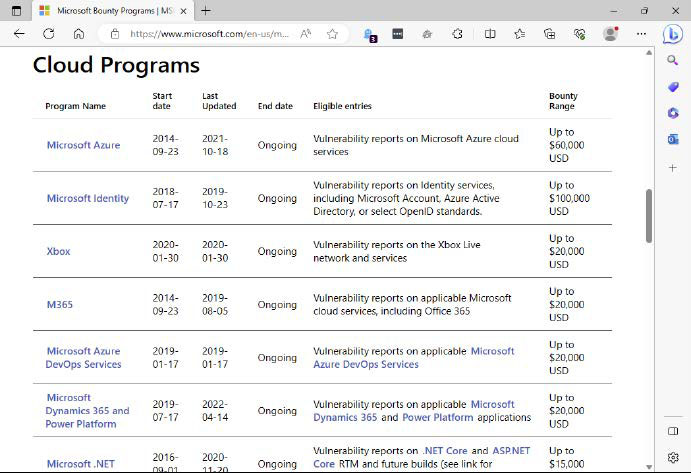
On its bug bounty website, Microsoft lists the maximum sums it will pay for newly discovered security holes. For some products, the finder can get up to 100,000 US dollars.
IDG
A zero-day security vulnerability has a high value on the black market. Six- to seven-figure sums are offered on the dark web for a newly detected and not yet patched security hole in Windows. But it is not only criminals who are interested in the vulnerabilities. In the past, secret services also exploited the gaps to carry out attacks on databases and infrastructure of other states.
The best-known example is Stuxnet: A computer worm reportedly developed by Israel and the USA was infiltrated into the systems of the Iranian nuclear program. Through several previously unknown security holes in Windows, it managed to take root in the system. It then manipulated the control of centrifuges for the production of fissile material so that they were defective after a short time, but did not issue an error message.
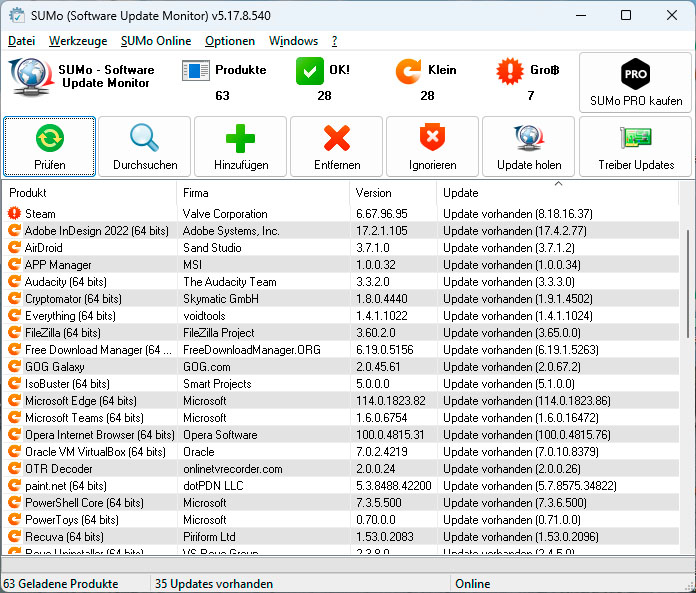
With the free tool Sumo, you can find out for which of your programmes updates are available and then install them specifically.
IDG
Governments and companies also use zero-day vulnerabilities for industrial espionage, i.e. to tap into plans for new developments, company data, and contact addresses. And finally, hacktivists also resort to this means to draw attention to their political or social goals.
Due to the high danger potential of zero-day flaws and the high sums paid for their disclosure, several large software companies have launched bug bounty programs. This “bounty for bugs” is paid by manufacturers like Microsoft for newly discovered security holes and other bugs in their operating systems and applications. The bounties are mostly based on the severity of the bug and range from three to six figures.
Attention: The 5 most dangerous Wi-Fi attacks, and how to fight them
How to detect zero-day attacksthe best windows antivirusNorton 360 Deluxe
When searching for malware, modern antivirus programs work not only with virus signatures, but also with heuristic methods and artificial intelligence. The manufacturers train them with the behavioral patterns of known malware in order to be able to detect new variants. However, this only works to a limited extent, as zero-day exploits always use different attack methods.
Behavior-based security solutions are often used in companies. Intrusion detection systems monitor log files and system information such as CPU utilization to identify conspicuous activities within a network and on individual computers. In this case, they issue a warning message or send an e-mail to the administrator. Intrusion prevention systems go one step further and automatically trigger countermeasures such as changes to the firewall configuration. However, such applications are very expensive and only suitable for businesses.
Finding information about new security vulnerabilitiesUntil the late 1990s, security vulnerabilities were not systematically recorded. But as new vulnerabilities were found in the rapidly growing number of Windows applications, two employees of the Mitre Corporation began to think about a sensible system for recording and managing them.
The US Mitre Corporation was founded in 1958 as a think tank for the US armed forces and today advises several American authorities on security issues. The non-profit organization is funded by CISA (Cybersecurity and Infrastructure Security Agency) and DHS (Department of Homeland Security).
The result of the deliberations was the CVE system (Common Vulnerabilities and Exposures) introduced in 1999. Since then, all security vulnerabilities have been given a CVE number or ID in the format CVE-XXXX-XXXXX. The first four characters indicate the year in which the vulnerability was catalogued, the digits behind it – there may be more than five – are the consecutive numbering of the vulnerability. The CVE system has meanwhile developed into an internationally recognised standard.
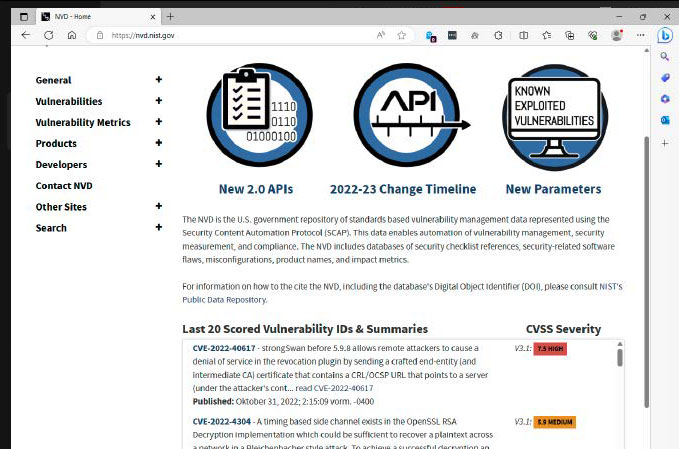
The National Vulnerability Database of the USA shows the 20 most recently found vulnerabilities and their CVE numbers. In addition, there is information on the mode of action and any available patches.
IDG
The Mitre Corporation has set up the website www.cve.org for the CVE database. There you can search for CVE numbers or for keywords such as “Windows Kernel”.
Alternatively, you can download the entire database with its more than 207,000 entries. Closely linked to the CVE website is the National Vulnerability Database (NVD). At https://nvd.nist.gov you will find the 20 most recently identified vulnerabilities, including some explanations and links to any available patches.
There you will also find an assessment of the danger of the vulnerability from “Low” to “Medium” to “High” and “Critical”. If an application you use appears there whose vulnerability is marked as “High” or “Critical”, check the manufacturer’s website to see if a patch is already available.
Microsoft also uses the CVE standard, but maintains its own list of newly detected vulnerabilities for its products at https://msrc.microsoft.com/update-guide/vulnerability The company distributes patches automatically via its monthly security updates; manual installation is not necessary.
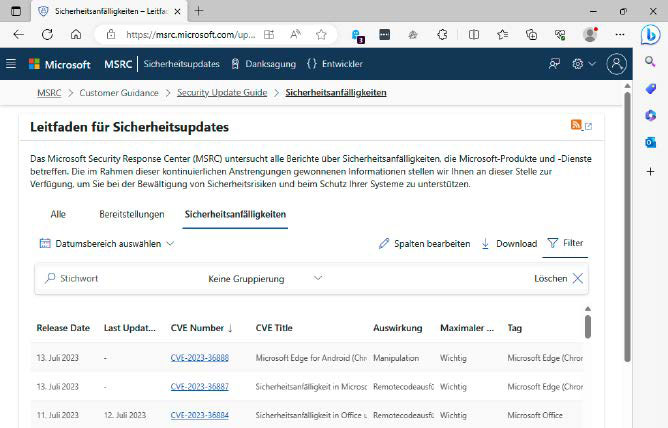
The company publishes newly found security vulnerabilities in its products in the Microsoft Security Response Center. You do not need to worry about installing the patches, this is done automatically.
IDG
How to protect yourself from zero-day exploitsZero-day attacks are not only directed against companies. Hacker groups sometimes also try to lure private users to malicious websites via widely distributed phishing attacks by e-mail, or to persuade them to install software with zero-day exploits, sometimes via scammy Google ads.
You can protect yourself with a few simple measures:
Install patches and updates as soon as they appear. Windows does this automatically by default, so you should not change anything. Use tools like Sumo to search for available updates for Windows applications.Only download software from trustworthy sources such as the manufacturer’s website.Only install the programs you actually need. The more software there is on the computer, the more potential vulnerabilities there are.Use a firewall. The Windows firewall is switched on by default and should not be deactivated.Find out about typical phishing tricks used by criminals.What to do if there are problems with updates?You should always install the monthly security updates and patches for Windows immediately in order to eliminate newly detected vulnerabilities.
However, the installation of a Windows update is not always successful. Sometimes the operating system aborts the process with an error message. In such a case, try the following:
1. Often, simply downloading the update files did not work. The solution is to empty the update cache and try again. The easiest way to do this is via the Windows troubleshooter: Call up the “Settings” in the Start menu and click on “Troubleshooting -‘ Other troubleshooting” in the “System” tab. Then click on “Run” for “Windows Update” and finally on “Close”. Then restart Windows by opening the “Run” window with the Windows-R key combination, typing the command shutdown /g and clicking “OK”. Then try to install the updates again.
2. Often there is simply no more space on the C: drive. Check this by opening the Explorer and selecting “This PC”. There should still be at least 32GB free on C:. If not, open the “Memory” options in the “Properties” under “System” and set the “Memory optimisation” switch to “On”. Click on “Clean-up recommendations” and look in particular at the items “Large or unused files” and “Unused apps”. You should also empty the Windows Recycle Bin.
Michael Crider/IDG
3. Try a manual installation of the update. Look in the “Settings” under “System -‘ Windows Update” as well as under “Update history” for a message about a failed update. Make a note of the KB number of the update and enter it in the Windows update catalogue at www.catalog.update.microsoft.com. Make sure that the update matches your Windows version, download it and install it manually.
4. If you use a virus scanner other than Microsoft’s Defender, you should uninstall it temporarily. Then restart Windows and try to run the update.
5. Disconnect any connected USB devices such as flash drives or external storage.
6. Open the Windows Control Panel (the easiest way to do this is by entering “control” in the search field of the taskbar) and call up the Device Manager. If entries with a question mark appear there, remove this hardware by right-clicking and selecting “Uninstall device”. Then try to run the update. When you restart, Windows will then recognize the devices again and install the latest drivers.
7. Update the drivers on your computer. Use a tool such as Driver Booster Free to check for outdated driver versions. Download the latest versions, set them up and try installing the Windows update again.
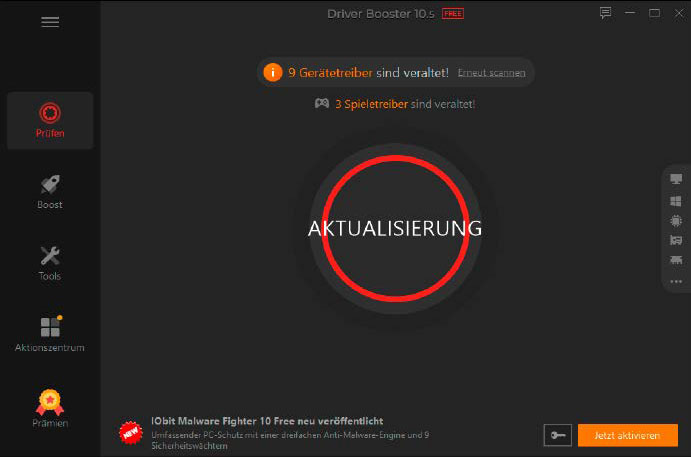
Make sure your drivers are up to date. For example, the tool Driver Booster Free can help you search for outdated versions.
IDG
This article was translated from German to English and originally appeared on pcwelt.de.